Multidimensional Body-Complex (6): 18 Human body Regulations
YWS
(3rd Edition, 2019)
--------Table of Contents--------
*Information Module System of Human Multidimensional Body-Complex Structure
A) Interactive System of Human Body Information Modules - Establishment of Structure and Types of Interaction
B) Interactive System of Human Body Information Modules - 18 Management Regulations and Technical Rules
*18 Management Regulations and Technical Rules
*Part One: The 5 Regulations for Human Body Modules
(Module Interaction Management Regulations)
1) Particle Convergence and Divergence Threshold Management Regulation
2) Displacement Pressure Threshold Management Regulation
3) Superimposed Pressure Threshold Management Regulation
4) Interaction Density Threshold Management Regulation
5) Reverse Development Threshold Management Regulation
*Part Two: The 13 Rules for Human Body Modules
(Module Interaction Technical Rules)
1) Spherical Structure Control Rule
2) Module Circuit System Rule
3) Module Spiral Development Rule
4) Module Point-to-Point Information Effect Rule
5) Rule for Interference by Increasing Information Particles
6) Rule Rule for Reducing Information Particle Entry
7) Rule for Introducing Fake Modules
8) Rule for Limiting Module Memory Storage Capacity
9) Module Invasion Rule
10) Module Hedging Rule
11) Trigger Module Mechanism
12) Hybrid Module Mechanism
13) Anti-Module AI Auto-Upgrade Mechanism
*Appendix: The Earth Human Body Rules Committee
a) What is the “Earth Human Body Rules Committee”?
b) History of the "Vehicle Particle Module Rules Research Committee"
c) History of the "SoC Research Committee"
d) Composition of the "Earth Human Body Rules Committee"
----------
Information Module System of Human Multidimensional Body-Complex Structure
The first 5 articles of "Multidimensional Body-Complex Structure" have introduced:
(1) Single Complex,
(2) Dual Complex,
(3) Multi-Complex,
(4) 18 Major Chakras,
(5) DNA Triplex & Cracking.
This article is the 6th one, introducing the "18 Human Body Regulations".
The full name of the 18 Human Body Regulations is:
"The Human Body Information Module Interaction System and Its 18 Management Regulations and Technical Rules."

The following is introduced in 2 parts.
A) The Interactive System of Human Body Information Modules — Establishment of Structure and Types of Interaction
Every component of the human body (either a material module or a non-material module) is an "information module," also known as a "consciousness module."
Information modules are composed of "information programs."
The essence of an "information program" is a "consciousness program," somewhat similar to what humans refer to as "AI program modules," but more advanced.
The establishment of human body information modules (or consciousness modules) is controlled by a program called YCCB.
This program is installed in the basic operating systems of the physical body and the 2nd to 10th spiritual bodies.
It is used to control the layered and functional establishment of corresponding information modules and to manage interactions between information modules.
For a detailed explanation of the human body information module interaction system, please refer to YWS' article "SoC AssessPoints (9) Lower Right Area: Module Exchange".
This article will not repeat the introduction.
This article focuses on introducing the "18 Management Regulations and Technical Rules of the Information Modules" in the following sections.
B) The Interactive System of Human Body Information Modules — 18 Management Regulations and Technical Rules
Information modules have a mechanism for mutual cooperation, managed according to globally accepted Earth rules, which are established by the "Earth Human Body Rules Committee" (*Appendix).
The Earth Human Body Rules Committee has issued a total of 18 information module management regulations and technical rules, forming the basic management rules for the operation of human information modules.
1) Overview of the 18 Management Regulations and Technical Rules
- a). Principles:
① The most fundamental principle of the hypnosis system is the "Principle of Not Being Detected". Therefore, hypnotic interference with the human body information system must be limited to a certain threshold; otherwise, it is easily detected. (For more on the hypnosis system, refer to YWS' article "What is Hypnotic Reincarnation")
② Different types of technical thresholds are set and adjusted after a certain number of technical tests on experimental subjects.
- b). Purposes:
① To prevent excessive interference that could cause a collapse between modules, resulting in irreversible damage and violating freewill.
② To study how to effectively guide and manage, ensuring that the interaction between templates is controlled within the intended hypnotic objectives without being detected.
- c). Background:
18 management regulations and technical rules were established to make the hypnosis game more enjoyable but not to the point of losing control. The T-Group previously had failure cases, realizing the need to establish rules for more effective, standardized, and better-managed hypnosis games. (For more on the T-Group, refer to YWS' article "What is Hypnotic Reincarnation")
2) Classification of the 18 Management Regulations and Technical Rules
- a). Macro management regulations for the interaction of human body information modules: 5 regulations.
- b). Micro technical rules for the interaction of human body information modules: 13 rules.
The following sections provide detailed explanations.
----
The 18 Management Regulations and Technical Rules
----
*Part One: The 5 Regulations for Human Body Modules
(Module Interaction Management Regulations)
----
1) Particle Convergence and Divergence Threshold Management Regulation:
Particle convergence and divergence: Information modules interact by converging and diverging information particles to receive and transmit information.
The interference method for information particle convergence and divergence cannot exceed a certain threshold; otherwise, it may affect information interaction and be easily detected.
In other words, excessive interference with information can cause excessive distortion in individual information reception and transmission, making it easily noticeable by the individual.
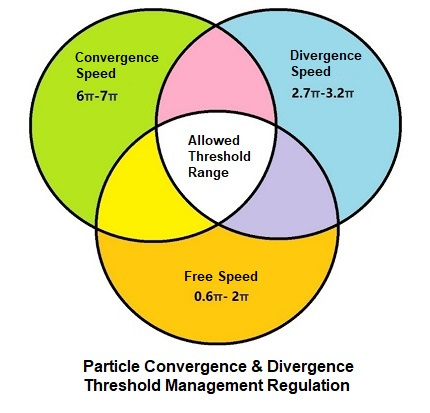
There are 3 thresholds:
(1) Convergence Speed (Information Entry Speed of the Module): 6π-7π. (π = relative speed multiplier)
This is the speed value of information transmission between information modules.
It represents the speed/vibration range value of numerous information particles moving from the information source module to the target module.
The vibration speed is relative, with the target relevance as the standard value (individual original value). Exceeding this critical limit will cause a chain reaction in module interaction, resulting in relatively irreversible consequences.
If the vibration range of the particle source or information source is too large, it will cause disharmonious differences in the vibration amplitude of each particle source and target.
This is equivalent to the information reception threshold of the target, including speed, capacity, depth, breadth, and frequency content.
(2) Divergence Speed (Information Clearing Speed of the Module): 2.7π-3.2π.
This is the speed value at which information particles are instantly cleared from the module under converging conditions.
If too fast, it leads to module splitting. If too slow, it results in insufficient momentum, losing to the original consciousness inertia, making divergence impossible.
(3) Free Speed (Information Status in the Module): 0.6π-2π.
This is the vibration amplitude of information particles in a relatively static state.
If too fast, it becomes unstable. If too slow, it solidifies and loses vitality, causing the information to become frozen and unable to be extracted.
It's like storing food in a refrigerator; if the temperature is too low, it freezes; if too high, it spoils.
The practical utility of this threshold includes storage state, standby state, and filtering state.
*Interference Methods:
Based on the natural state of the individual’s information particle convergence and divergence (individual original value = standard value), various interference combinations are used (as shown in the diagram). However, they are controlled within the above threshold range, it can achieve the purpose of hypnosis while remaining undetected.
----
2) Displacement Pressure Threshold Management Regulation:
Displacement pressure is a type of interference method that applies pressure to the pathways between each information module. This pressure can cause displacement of the pathways.
If the interference exceeds the threshold, it will result in severe consequences.
For example, instead of information being sent from A to B, excessive pressure might send it to M, which could be noticed by the individual, thus defeating the purpose of covert interference. Additionally, this could trigger the module's self-correction mechanism.
*Purpose of Setting the Displacement Threshold Range:
(1) To prevent detection by the individual.
(2) To prevent the activation of the module's self-correction mechanism.
If the pressure is too low, it will have no effect.
*There is one threshold:
A displacement value of 1.5-3.5 times.
This is a conservative threshold derived from AI deep learning and represents the overall average value for humans. This threshold can be customized based on individual circumstances.
----
3) Superimposed Pressure Threshold Management Regulation:
Superimposition: refers to adding an interference directive module on top of a natural module, which is considered a non-natural module, also known as a superimposed module.
Superimposed pressure: refers to the different pressures generated when different superimposed module structures interact.
*Interference Methods:
Superimposed modules can include directives that affect the interaction of information between modules. However, modules can exhibit a superimposition effect, resulting in a range of fluctuations. If the interference exceeds a certain range, it will lead to the overall collapse or malfunction of the module.
*There are three thresholds:
(1) Serial Superimposition: Approximately 6t (the overall average value for humans, same as below).
(2) Parallel Superimposition: Approximately 15t.
(3) Compound Superimposition: Approximately 32t.
(4) Total Composite Value: Approximately 53t.
*Parameter Unit: t = the multiplier value of pressure output from module superimposition.
*Pressure: When interference directives are input into the module, they create a relative difference value distinct from the natural state.
Differences will generate a repulsive force from the module's freewill.
If the repulsive force exceeds the threshold range, it will result in a module strike.
----
4) Interaction Density Threshold Management Regulation:
Interaction density threshold: refers to the network density of multiple connections formed between various information modules, constituting their composite structure.
These connections have multiple functions: module interaction, cooperation, information circuitry, addition, transformation, transmission, energy transfer, and other interference programs, similar to inserting tubes.
In a natural state, the connections between modules are relatively few, with just a few simple lines facilitating efficient transmission.

*Interference Methods:
The T-Group has added many connections, resembling a network of highways that loop around extensively.
The purpose of this is to cause information distortion, impact speed, enable monitoring, and facilitate processing, among other things.
However, if the connection density is too high, it will lead to energy depletion.
Therefore, the network's density must be built within an effective range.
*There is one threshold:
A density value of 17 times.
This means that the network density should not exceed 17 times that of the natural network density.
----
5) Reverse Development Threshold Management Regulation:
The reverse development threshold is represented as a triangular curve graph.
There are three thresholds:
(1) Natural State (Purely Natural, Unoptimized): A value of 1 or 0 (relative base value), set as x, corresponding to the natural value of the individual.
(2) Optimal Plan in Normal State (Best Suited to Individual Interests): +7.5x. This represents potential for development.
(3) Optimal Plan in Management State (Best Suited to T-Group Interests): -9x. This represents the compressible space.
The average measurable range for humans is from +7.5x to -9x, as described above.
*Sample Data from Experimental Subjects:
- Test Subject 2: +3x (Range: +5x to -17x).
- Test Subject 1: +1.5x (Range: +3x to -25x).
- Test Subject 3: -2x (Range: +7x to -10x).
Test Subject 3 - The measurement data graph for Test Subject 3 is as follows:
a red curve along the time axis from the bottom up, resembling a winding mountain road or a spring. It shows a highly effortful consciousness pattern, but the effort does not match the results, indicating a disadvantageous situation.
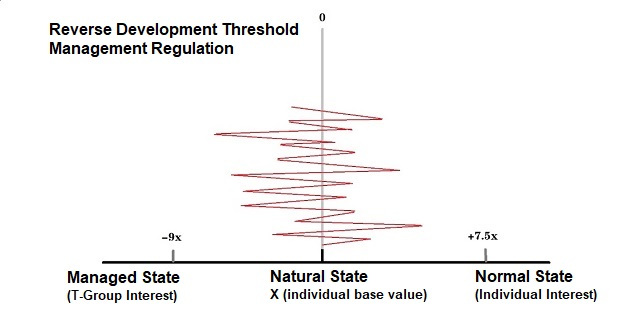
All research projects use the ratio curve of these three thresholds for objective qualification and broad application as a reference.
The ratio between 1 and 2 is also dynamic, adjusted according to the state of confrontation between the will of the hypnotist and the hypnotized. This ensures balance and maximizes management for macro control.
Exceeding the threshold makes reverse development for an individual difficult, such as when someone becomes comatose and is unlikely to regain consciousness.
Conversely, if development is too rapid, the individual may become too free and uncontrollable.
----
Part Two: The 13 Rules for Human Body Modules
(Module Interaction Technical Rules)
----
1) Spherical Structure Control Rule
*Spherical Structure:
Many information modules are located at different positions within a sphere, moving slowly. During the process of module interaction, the ultimate information entry and exit points are located at the top and bottom ends of the sphere, forming entry and exit points at the head and foot of the axis. The two ends extend outwards as pointed tails, forming the overall interaction model.
All modules are connected in parallel to form a sphere, through which all information undergoes processing and filtering.
The spherical structure thus created generates a pulling force that aggregates all modules together.
- Purpose: To effectively manage the inflow and outflow of all module information.
Each module develops automatically during motion.
- Sphere: It can constrain the development of modules, keeping them limited within a confined area, which is conducive to controlling the module's development.
Without the constraint of a sphere, modules may take on various shapes. The sphere can either tighten or loosen.
Artificially tightening the sphere can cause module collisions, which may generate reverse information, leading to fractures.
As modules develop, they grow larger. If space is insufficient, collisions and compression occur.
*Interference Methods:
The AI control center of the spherical structure will automatically loosen the sphere according to the pressure of compression to allow it to expand; otherwise, reverse information fractures will occur.
- Purpose: To keep all modules in an asynchronous and fractured state, thus suppressing their development.
If the pressure is too great and the sphere does not loosen, it will be breached. Therefore, it is necessary to refer to a threshold to keep it within a controllable range.
- Summary: All natural modules have self-development laws during operation. Without the control of the sphere, they will lose control.
- Final Purpose: To slow down the natural development of humans so that they cannot advance.
*Pressure Threshold:
- Overall human threshold: 3-7 times. The relative structural pressure value, denoted as “s”, between individual modules varies.
- Test Subject 2: 3.5
- Test Subject 3: 4.7
- Test Subject 1: 2.7 (the spherical structure still exists and has not been destroyed, making it difficult to revert to 1).
- Actual Control Power Value:
The overall comprehensive value of modules, including fusion, synchronicity, and stability, will form a confrontation with the actual control power of the spherical management mechanism.
For example:
- Test Subject 1: = Original control power 1 / Module comprehensive value 2 = 1/2.
The higher the comprehensive value of the module, the stronger the resistance.
- Overall human value: 1. As a relative base value = original control power.
For stronger resistance, the comprehensive value of the module is set higher.
*Sample Data from Experimental Subjects:
- Test Subject 2: 1/1.5
- Test Subject 3: 1/1.1
- Test Subject 1: 1/2.2
*How to Break It:
The spherical structure is a collective control mechanism. Breaking the sphere requires a collective consciousness elevation to cause the device to malfunction, or violently destroying the individual sphere.
The simplest violent method: The sphere is already bound to the module, so violently breaking the sphere would also destroy the module, requiring some skill. After DNA is cracked, the core structure of this sphere will also automatically fail synchronously. However, as long as one does not exit the reincarnation system, no matter how high the consciousness intensity, it can only infinitely approach 1, but cannot render it completely ineffective.
----
2) Module Circuit System Rule
*Module Circuit System:
During the interaction process, a portion of the information returns to the module, where the module records it.
When information passes through a module, the reference values or patterns formed are recorded within the module through the information circuit, thereby allowing the module to proceed with subsequent upgrades. This is a characteristic of module interaction.
These pieces of information will form a shared information circuit throughout the entire module interaction to enhance overall operational efficiency.
Due to this characteristic, the T-Group imposes certain restrictions on the shared information circuit to slow down the information sharing speed and cause confusion in the information circuit system.
*T-Group's Restriction Methods:
- Slowing Down: By adding different wiring methods to form a complex network, slowing down the information circuit, and causing certain information to not reach its destination, the overall system's reflux efficiency is significantly restricted.
- Disruption: Some connections are deliberately created to cause errors.
For example, the information of module A may return to module B during reflux, resulting in misalignment. It's like deliberately sending a courier package to the wrong address, reducing the overall efficiency of the modules (as shown in the diagram). This greatly reduces the self-learning and self-upgrading functions of the module.
*Density Threshold:
As mentioned in the Interaction Density Threshold of the 4th Management Regulation.
- Humans: 17 times threshold.
*Sample Data from Experimental Subjects:
- Test Subject 2: 9
- Test Subject 3: 12
- Test Subject 1: 2
*How to Break It:
Improve the integration between modules to enable information to reflux at the fastest speed.
- Integration: Primarily related to SoC (Strength of Consciousness).
For example:
The degree of module development, the operation among modules, and other SoC values.
This is also a structural mechanism, not like a switch. No matter how high the SoC is, it can only infinitely approach the natural value, unless one exits the hypnotic reincarnation system.
After DNA is cracked, it will naturally fail synchronously, and modules will automatically reorganize to return to their natural state.
----
3) Module Spiral Development Rule
*Module Spiral Development Rule:
During interaction, modules will form a spiral promotion effect, where all modules create a spiral ascending promotion, akin to a superposition effect.
*Interference Methods:
The T-Group targets this characteristic for effective suppression.
Natural development involves parallel spirals, but the T-Group changes the parallel structure to a serial structure, significantly reducing efficiency.
The T-Group establishes a serial, multi-layered, fishbone-like central information system among modules.
- Original System: All modules are arranged in an orderly, equal, and parallel system.
For example: if one module sends out a program/experience/rule, it can enhance the efficiency of all modules, allowing them to be simultaneously and parallelly promoted.
- T-Group's Fishbone Structure: Promotion can only be received sequentially from bottom to top, one by one, to limit interaction efficiency.
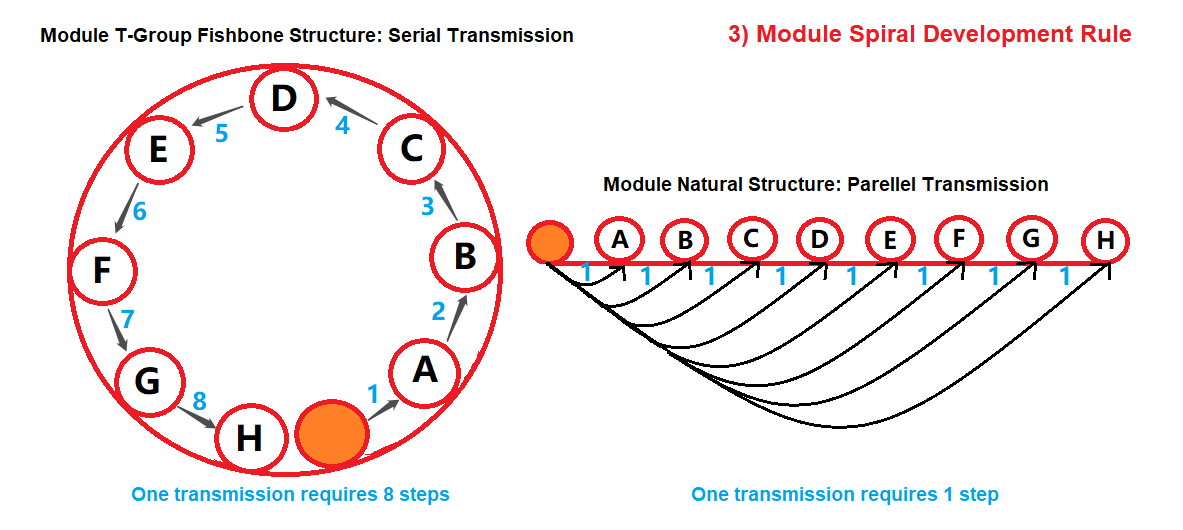
*Spiral Promotion Value:
Efficiency ratio at the highest is 1:1, natural ratio.
- Average Human Value: 1/5 to 1/8
*Sample Data from Experimental Subjects:
- Test Subject 2: 1/4
- Test Subject 3: 1/5
- Test Subject 1: 1/2
*How to Break It:
High SoC can naturally break through structural limitations and output directly through spiral enhancement.
- Complete Breakthrough: Since it's structurally bound, unless one exits the hypnotic reincarnation system, it can only infinitely approach 1.
After DNA is cracked, this structure will fail.
----
4) Module Point-to-Point Information Effect Rule
*Module Point-to-Point Information Effect:
Information between modules does not require direct connections; instead, when the same information frequency is generated, it results in non-connected remote synchronous information sensing, similar to quantum entanglement. Due to this being a form of remote information transmission, the T-Group cannot interfere using conventional connections.
*Interference Methods:
However, the T-Group can record the triggered information by initiating sensing and capturing the information.
Once the information is captured, it is fed back into the AI transmitter to simulate the signal, generating interference waves that disrupt the seamless transmission of information.
The weakness of this method is that it cannot preemptively interfere and can only react after the information has appeared. Hence, it is a passive interference mechanism, incapable of proactive interference.
*Interference Process:
The system captures and synchronizes the information frequency, replicates, deforms, and distorts the information, then sends it back to the original source, leading to confusion and distortion of the information for the individual.
- Degree of Original Information Distortion: If the distortion is too minor, it has little impact. If too great, it is easily noticed. Therefore, the distortion must adhere to the inherent logical relationships within the information to effectively achieve subtle distortion.
*How to Counteract?
External interference cannot completely eliminate remote transmission, but it can limit its effectiveness to some extent. SoC remains the primary means of counteracting this.
*Point-to-Point Information Interference Threshold:
- Human Average: A misalignment range of 0.5 to 3.5 times, equivalent to a 50%-350% distortion range based on the original information's 100% benchmark.
- In other words: Interference can result in 50%-350% information distortion or misalignment.
*Sample Detection Data:
- Test Subject No. 2: 0.3
- Test Subject No. 3: 0.3
- Test Subject No. 1: 0.1
- Test Subject No. 4: 4.0-4.5
- Test Subject No. 17: 5
- Test Subject No. 18: 4-6
- Test Subject No. 11: 1.5-2
- Test Subject No. 13: 3.5
- Test Subject No. 16: 1.5
- Test Subject No. 5: 1-1.5
- Test Subject No. 6: 0.7
- Test Subject No. 15: 0.5
----
5) Rule for Interference by Increasing Information Particles
*Interference by Increasing Information Particles:
When a large number of information particles enter the module linkage system, it interferes with the system by randomly generating impurities and mixing them into the information channels. Consequently, it increases the operating pressure, workload, and processing time of the modules, as well as the difficulty. This leads to the incorporation of unrelated impurities into the original information.
The T-Group employs this kind of interference device, which, upon detecting information entering the module, automatically generates impurity information using AI to mix into the module.
The goal is to increase the processing time and workload of the module, reducing the accuracy of information, increasing redundant information, and lowering processing efficiency.
This interference system has AI learning mechanisms capable of analyzing individual characteristics for deep learning, producing personalized impurities, and attempting to prevent individuals from noticing.
The system will also learn based on information characteristics, analyzing the probability of certain information types over the long term.
Example:
If an individual frequently receives certain types of information, the interference device, after detecting this habit, will implement specialized interference.
The primary aim is to slow down and reduce the efficiency of the module's self-learning and auto-upgrading processes. Otherwise, the module would auto-learn and upgrade based on frequently received information.
(This is akin to a small AI robot interfering with a larger AI robot.)
*Interference Rules:
There is a defined range for the quantity of information impurities introduced. If too low, the impact is negligible; if too high, it is easily noticed.
*Interference Threshold:
- Human Average: An increase in the range of 0.2-2 times.
*Sample Detection Data:
- Test Subject No. 2: 1 (up to 1x increase)
- Test Subject No. 3: 2.5 (in a specific tendency area)
- Test Subject No. 1: 0.5
- Test Subject No. 4: 1.8
- Test Subject No. 5: 2.7
- Test Subject No. 6: 1.2
- Test Subject No. 7: 1.9
- Test Subject No. 16: 1.5
----
6) Rule for Reducing Information Particle Entry
*Rules for Reducing Information Particle Entry:
This involves a barrier-like filtering system that results in the distortion and incompleteness of information particles, mainly based on individual characteristics and tendencies.
The principle is to create information filters according to individual subjective tendencies, subconscious inclinations, and fixed tendencies to filter and mask incoming information.
The filtering and interference devices are AI-driven, emphasizing interconnectivity and scalability.
Depending on individual characteristics and tendencies, there are a range of expansion values.
For instance: if an individual does not accept D, it will expand to D and E.
*Expansion Threshold:
Too broad would be easily noticed. Thus, it should give individuals a reasonable and natural feeling.
- Human Average: ±0.3 to ±2, similar to an upper and lower percentage range.
*Sample Detection Data:
- Test Subject No. 2: ±0.3 (30% upward and downward fluctuation range)
- Test Subject No. 3: ±0.3
- Test Subject No. 1: ±0.1
- Test Subject No. 4: ±1
- Test Subject No. 5: ±0.8
- Test Subject No. 6: ±0.5
- Test Subject No. 7: ±0.8
- Test Subject No. 16: ±0.4
----
7) Rule for Introducing Fake Modules
*Introduction of Fake Modules:
During the linkage of various modules, fake modules (clone modules) are introduced to cause interference.
This method involves a series of monitoring activities to clone the native module and initialize it purely as a mirroring interference tactic.
The virtual module clones automatically based on the native module, backing up cloned data and subtly modifying synchronous data.
This rule is related to implants and uses clone modules to support the implants. Cloning involves not only modules but also operating rules and parameters.
- The cloning mechanism: involves learning and copying the native module's program to obtain information and data, which can aid implants.
The primary goal is to make it difficult for the native module to detect external interference.
Since the original module is irreplaceable, the fake module can blend false information into the native modules or provide information to the implants, assisting them.
The introduction of false information must have a defined range - too much will be detected by the module, too little is ineffective.
*Fake Information Introduction Threshold:
- Human Average: 1-5 times the original value, referencing the individual relative multiplication value based on the identification mechanism of the native module.
*Sample Detection Data:
- Test Subject No. 2: 0.5 (increase range 50%)
- Test Subject No. 3: 0.8
- Test Subject No. 1: 0.1
- Test Subject No. 4: 1.3
- Test Subject No. 5: 1.8
- Test Subject No. 6: 1
- Test Subject No. 7: 1.4
- Test Subject No. 16: 1.2
----
8) Rule for Limiting Module Memory Storage Capacity
*Module Memory Storage Capacity:
A module has the ability to store memory, similar to computer memory, recording characteristics of the processed information.
Under normal circumstances, a piece of memory that is not recalled will gradually be forgotten or faded over time (this is not true forgetting; it is more of a fading since memory never truly disappears).
*Interference Methods by T-Group:
T-Group imposes limitations on the memory functions of the module to interfere with its memory capacity.
For example: some memories may have an original forgetting period (fading period) of, say, 5 years, which T-Group may shorten to 3 years.
- Limitation Methods:
T-Group inputs a large amount of useless data into the module, reducing the module's processing efficiency.
Through this information interference and confusion, the memory storage capacity is compressed.
This is similar to filling a memory warehouse with a lot of garbage, reducing the available space. From the module's perspective, the warehouse is full of boxes, but in reality, the boxes are empty or contain useless information.
For instance: "chicken soup for the soul" content appears to be noble but actually has little practical value.
Native modules have automatic cleaning programs, but the recognition and cleaning capabilities vary from individual to individual. When efficiency is low, the cleaning might be done indiscriminately, meaning useful and useless information may both be removed.

*Threshold:
The goal is to shorten the memory fading period as much as possible without being detected, thus achieving the purpose of interfering with human memory capacity.
- Human average: Efficiency multiplier between -2 and -8. Relative individual values.
*Sample Detection Data:
- Test Subject 2: -3.5 (shortened by 3.5 times)
- Test Subject 3: -4
- Test Subject 1: -1
- Test Subject 4: -5
- Test Subject 5: -4.5
- Test Subject 6: -4.3
- Test Subject 7: -4.5
- Test Subject 16: -4.2
----
9) Module Invasion Rule
*Module Invasion:
The module linkage manager periodically introduces virus information particles.
Through the monitoring of the linkage system, the AI system simulates module characteristics, regularly conducts virus checks, and introduces a large number of virus particles into the module to detect the number of vulnerabilities.
*Threshold:
The detection process must not allow the individual to become aware; a controllable threshold range is required.
If the interference is too strong, vulnerabilities may be noticed by the individual, turning the test into a free checkup.
The goal is to detect and utilize vulnerabilities without the individual noticing.
The threshold range is controlled based on the different characteristics of each module.
- Human average: 2-5Ω (destructive intensity unit level), which is proportional to the module's tolerance.
*Effects on Module:
- 1Ω: Processing is chaotic but still manageable.
- 2Ω: Data processing errors occur but do not affect overall information interpretation.
- 3Ω: More errors appear, affecting the fluency of information interpretation.
- 4Ω: Minor logical errors occur, and information accuracy slightly declines.
- 5Ω: Major logical errors occur, and information accuracy significantly drops, with details being lost.
*Sample Data from Tests:
- Test Subject 2: 5 (module recognition ability = virus tolerance. Above 5Ω, it's easily detected unless customized manually).
- Test Subject 3: 4
- Test Subject 1: 5
- Test Subject 4: 2.5 (2.5Ω is sufficient for detection purposes).
- Test Subject 5: 3.2
- Test Subject 6: 3.5
- Test Subject 7: 2.8
- Test Subject 16: 4
----
10) Module Hedging Rule
*Module Hedging:
The principle is to use the inherent characteristics of native modules to create conflicts, thereby offsetting the module's execution power. This is equivalent to sowing discord, leading to internal conflict and self-consumption (internal friction).
*Interference Rule:
The interference control mechanism of T-Group will look for the module with the greatest conflict and perform data hedging to create contradictions.
During the hedging process, if the conflict is too significant, the individual will enter a self-reflection mechanism. Native modules will automatically begin recalculating the degree of integration, and a self-promotion mechanism will be activated to calculate, reflect, and upgrade the integration degree between the two conflicting modules, similar to the principle of extremes leading to opposites.
Therefore, T-Group's interference control must avoid causing excessively fierce module conflicts to prevent triggering the module's native self-reflection mechanism.

*Threshold:
- Human average: 2-5Φ (conflict intensity unit level), which is proportional to the module's tolerance.
*Sample Data from Tests:
- Test Subject 2: 4.5 (conflict intensity multiplier)
- Test Subject 3: 3 (3x is sufficient to achieve interference)
- Test Subject 1: 5
- Test Subject 4: 3.2
- Test Subject 5: 3
- Test Subject 6: 3.8
- Test Subject 7: 3
- Test Subject 16: 3.8
----
11) Trigger Module Mechanism
*Trigger Module Mechanism:
Modules have a trigger management mechanism, and all modules have trigger values. When incoming information reaches the trigger value, the module will start operating. The overall system manages these trigger values for each module. The native system is orderly, with high coordination among the various modules.
T-Group modifies the system’s trigger values so that the modules do not activate at the optimal times, ultimately reducing the overall operating efficiency.
Each module has a different trigger value (main modules in the SoC profile).
T-Group adjusts these values, either increasing or decreasing them, to make the triggering occur earlier or later.

*Trigger Efficiency Limitation Threshold:
- Human average: 2-5 times (decrease factor), inverse value.
- If too high, it may cause the module's operation to become chaotic, putting the individual in a state of significant setback, which is easily detected.
- If too low, it lacks effective control.
*Sample Data from Tests:
- Test Subject 2: 1.5 (reduced by 1.5 times)
- Test Subject 3: 2.1
- Test Subject 1: 0.7
- Test Subject 4: 2
- Test Subject 5: 2
- Test Subject 6: 2.1
- Test Subject 7: 2.1
- Test Subject 16: 2
----
12) Hybrid Module Mechanism
*Hybrid Module Mechanism:
This involves mixing the interference mechanisms mentioned above to optimize control, ensuring that various control methods are in their best states. It interferes with the final output of the information after it has been organized and integrated.
- Includes Two Programs:
(1). Effective management of the control mechanisms in the above rules.
(2). Interference with the final output of the organized and integrated information.
T-Group has different departments responsible for the specific regulation of different module values. Department heads oversee macro-control of the overall values.
This is related to the “5th Management Regulation: Reverse Development Threshold”, sharing the same thresholds.
(1). Natural State (pure natural, non-optimized): Set to a relative base value of 1 or 0, relative to the individual's natural value, denoted as x.
(2). Optimal Normal State (in the best interest of the individual): +7.5x, representing the potential development space.
(3). Optimal Managed State (in the best interest of T-Group): -9x, representing the compressible space.
*Threshold:
- Human average measurable range: +7.5x to -9x. Focuses primarily on controlling negative values.
*Sample Data from Tests:
- Test Subject 2: +3x (range: +5x to -17x)
- Test Subject 3: -2x (range: +7x to -10x)
- Test Subject 1: +1.5x (range: +3x to -25x)
- Test Subject 4: -1x to -2x (range: +7.5x to -11x)
- Test Subject 5: -1.2x to -1.5x (range: +7x to -9x)
- Test Subject 6: -0.8x to -1x (range: +8x to -12x)
- Test Subject 7: -2x (range: +8x to -9x)
- Test Subject 16: -0.5x (range: +6x to -12x)
----
13) Anti-Module AI Auto-Upgrade Mechanism
*Module AI Auto-Upgrade Mechanism:
The AI system of the native module in human robotic body will automatically upgrade in a natural state. In other words, when foreign information is detected to interfere with or manipulate the module, the module will automatically learn and upgrade itself.
*Anti-Module AI Auto-Upgrade:
T-Group interferes with this mechanism to prevent modules from upgrading during interaction (preventing the human robotic body from automatic learning and upgrading).
The interference method involves controlling the threshold range through the Threshold Control Center to prevent the module from being activated by the threshold, thus preventing automatic upgrades. This control ensures that the upgrade function remains dormant, keeping the module in a robot-like state.

*Threshold:
Comprehensive value, with more emphasis on management mechanisms. Linked to the “5th Management Regulation - Reverse Development Threshold”, and is more comprehensive than Rule 12, including positive values.
If an individual shows signs of awakening, the positive value will be adjusted to put the individual in a pseudo-enhanced state.
For example: Test Subject 3’s pseudo-positive state and pseudo-enhancement status, where the comprehensive SoC value does not improve, making it difficult for the individual to identify this fake enhancement.
- Two Key Focuses for Comprehensive Thresholds:
(1). Regulation 5: Mainly involves an irreversible threshold range.
(2). Rule 13: Mainly aims to prevent the activation of the module’s auto-upgrade ability.
- Human average: ±4x.
The average value for the activated threshold range, along with other comprehensive factors, requires different departments of T-Group to separately control other factors.
*Sample Data from Tests:
- Test Subject 2: +3x/±2.8x
- Test Subject 3: -2x/±5.8x (pseudo-enhanced state)
- Test Subject 1: +1.5x to +2x/±1.7x (old value, no latest value; data for this subject in the T-Group’s database has not been updated for a long time due to being breached by the subject, and unable to find a threshold range to update).
- Test Subject 4: -1x to -2x/±6x
- Test Subject 5: -1.2x to -1.5x/±5.5x
- Test Subject 6: -0.8x to -1x/±5x
- Test Subject 7: -2x/±6x
- Test Subject 16: -0.5x/±5x
*Note:
The above values are just averages and comprehensive values.
*Individual Actual Situations:
Individuals may have specific strengths and values in certain areas that can break through the limitations of the average and comprehensive values, triggering the automatic learning and upgrade mechanism.
Therefore, paying attention to enhancing one’s strengths and using them to overcome weaknesses is also an effective awakening strategy.
----
Appendix: Earth Human Body Rules Committee
a). What is the “Earth Human Body Rules Committee?
Full name: “Earth Branch of the Vehicle Particle Module Rules Research Committee”.
- (1) “Vehicle Particle Module Rules Research Committee”:
This is an organization that studies and manages the interactivity of game vehicle modules. “Game vehicle”, referred to by humans as “body”, is a type of robot.
- Research and management scope: All hypnotic planets (including those operated by T-Group, S-Group, etc.).
This is a large research organization with a core committee of 12 members and more than 10,000 employees distributed across different hypnotic planets. Members include various types of beings, such as humanoids, reptiles, etc.
- (2) “Earth Human Body Rules Committee”:
This is the Earth branch of the “Vehicle Particle Module Rules Research Committee”. The “game vehicle” of Earth human is referred to as the “multi-dimensional body-complex” by Homo sapient.
b). History of the “Vehicle Module Rules Research Committee”
It originated as a separate entity from the “SoC Research and Management Committee” (an independent research organization not affiliated with T-Group).
It started on a smaller scale but has grown through several changes and developments into a dedicated and sizable system closely tied to SoC research. Most of its technical personnel come from T-Group staff and related star alliances.
c). History of the “SoC Research and Management Committee”
Initially, it was an independent technical organization specializing in studying SoC with a small number of members.
After the emergence of 1-Group, resources were combined.
Subsequently, the organization’s main focus became the development and management projects of hypnotic planets, which account for 80% of its business, primarily researching “consciousness limitation” technology.
Other non-hypnotic fields projects account for approximately 20% of its business, focusing mainly on “consciousness expansion” technology.
d). Composition of the “Earth Human Body Rules Committee”
The “Earth Human Body Rules Committee” consists of fewer than 2,000 employees, with a core committee of 9 members. It is relatively low-key, does not make its presence known publicly, and is a highly secretive organization.
The committee primarily focuses on research, mainly on projects assigned by T-Group, but it maintains a high level of independence.
- Management model:
Core members operate on a rotational basis, with the committee chair elected by the committee. The general members remain relatively fixed, similar to the management model of T-Group. The SoC of core members is generally above 9.
T-Group does not heavily manage this committee, mainly sending project managers to assign projects.
Project managers from T-Group and the committee chair jointly lead projects, while the other 8 members are relatively free and independent, often engaging in their preferred research and occasionally collaborating with other organizations.
T-Group’s strategy for interfering with the SoC of hypnotic planets is primarily based on and informed by the technologies provided by this committee.
---
*Note 1: All testing data in this document is from 2019.
*Note 2: For some test subjects, the SoC values assessed in the same year can be cross-referenced with the document published by YWS "SoC AssessPoints: Sample Testing Data 20190317".
----
YWS
©Copyright reserved.






